Misbehave
题目分类:
< 随机数 > <自定义memcmp>
题目信息:
Author: mikanami
There’s something strange about this binary file…
Hints for beginners…
The attached file is an ELF executable for x86-64 Linux. Running it and entering the correct FLAG will display Correct!. Use tools like Ghidra or IDA Free to get an overview of the process.
Use gdb to observe its behavior while running. You don’t need to fully understand every single process. Sometimes, it’s enough to identify the inputs and outputs.
题目总览:
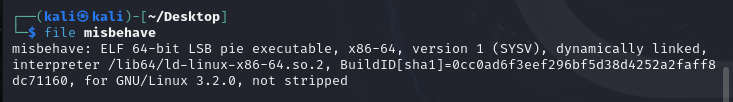
file查看文件信息
扔IDA看逻辑:
1 | int __fastcall main(int argc, const char **argv, const char **envp) |
看初始化v4:
1 | char *__fastcall init(__int64 offset_target_23B7, __int64 offset_source_22)//这里修改传参名称,结合以下函数功能,23B7和22是main函数传入 |
随机数生成函数,因为v5的变化在检查循环内,所以每个循环都会更新state的值
1 | __int64 gen_rand() |
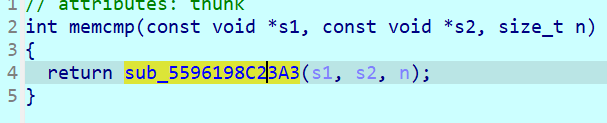
很好的memcmp,可能当作strcmp了(x
在调试起来发现,链接了另一个函数
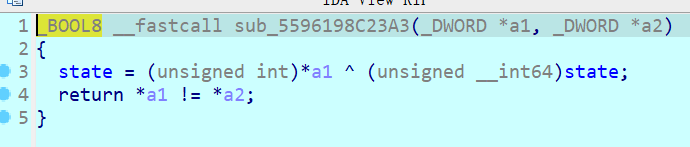
这里对state也有操作,每组数第一个数对state异或
题目解决:
state初始值:
state = 0xFEEDF00DDEADBEEFLL;
密文知道了:
1 | enflag = [ |
没有在memcmp被异或的state中间值:
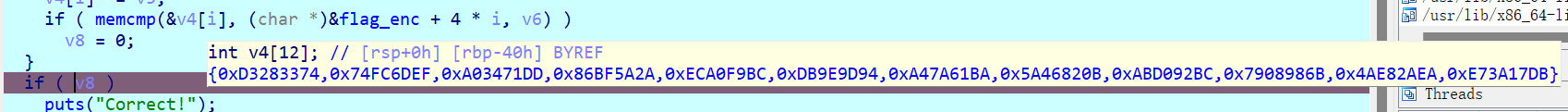
1 | initia = '19BC7C670' |
在memcmp自定义函数中,第i+1个state会与第i组明文异或*
1 | state_init = 0xFEEDF00DDEADBEEF |
测试一下
一些别的:
グローバル変数
stateを初期化しています。そして、init関数内部のアドレスloc_1381からの相対オフセットを使ったアドレスへ、uint64_t値を書き込んでいます。計算すると、書き換え先のアドレスはmemcmp@got、書き換え後の内容は13A3の関数でした。つまり、main関数ではmemcmp関数ではなく13A3の関数を呼び出します!初始化全局变量状态。然后,使用 init 函数内地址 loc_1381 的相对偏移量将 uint64_t 值写入该地址。我算了一下,要重写的地址是memcmp@got,重写后的内容是函数13A3。也就是说,main函数调用的是13A3函数,而不是memcmp函数!
4 字节 memcmp 的比较的同时,全局变量状态将通过与第一个参数的 XOR 结果进行更新。
Warmup SQLite
题目分类
< SQLite opcode>
题目信息
Author: mikitorium08
Let’s get familiar with SQLite’s bytecode
题目分析
一开始没怎么搞懂readme里在说什么
1 | # Warmup SQLite |
看python文件:
1 | import sqlite3 |
检测flag是否64位,且match('^[a-zA-Z0-9_=}{"]+$', s),之后对flag处理,与res比较
对flag的check应该是在db里面,
1 | #sqlite3 Python library:使用 sqlite3 库来与 SQLite 数据库进行交互,并使用 EXPLAIN 获取 SQL 查询的 opcode 列表。 |
看到文档里crazyman贴了一个:
https://www.sqlite.org/opcode.html
往下滑滑,找到一个很类似的东西,
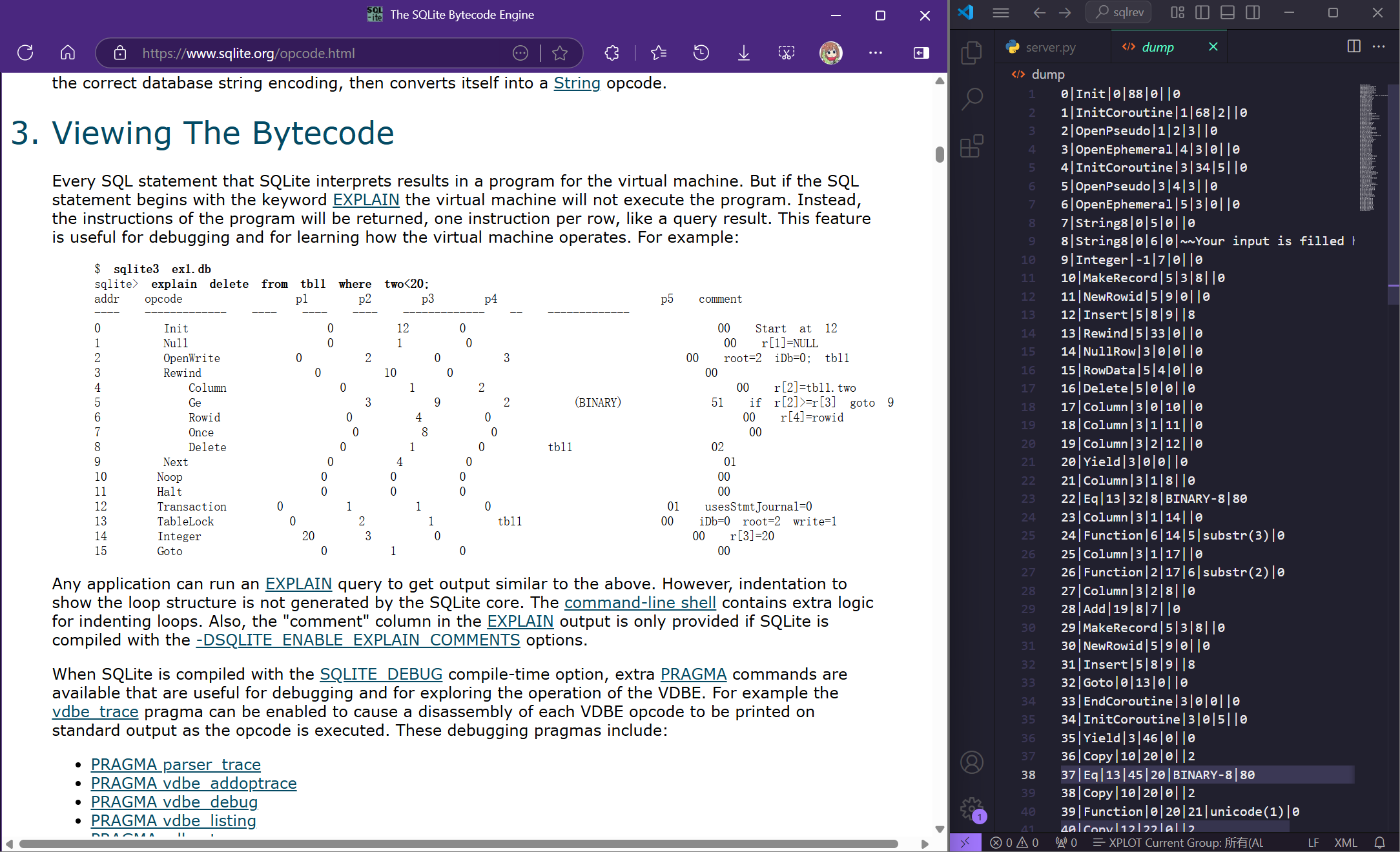
1 | $ sqlite3 ex1.db |
所以dump应该是对db文件的转储,所以问题变成了,如何将 sqlite opcade 转换为可以阅读的常见指令类型(比如右侧comment)
if SQLite is compiled with the -DSQLITE_ENABLE_EXPLAIN_COMMENTS options. (乐)
难蚌

照着opcode一点一点写规则(?
1 | def opcode_to_description(opcode, p1, p2, p3, p4, p5): |
一点一点扣规则(?
最后的integer似乎是寄存器?找一些操作行为,比如Ge、add、Multiply
1 | 57|Multiply|30|29|24||0 |
根据寄存器的内容读取第 55 条到第 66 条指令时,循环了 10 次计算 ((something * 7) + 2) % 256
本想着直接爆破来着(x 下面是一个数学方法,
一些别的
ctf_writeups/2024/tsgctf/README.md at master · moratorium08/ctf_writeups
这个师傅SQL恢复的非常好:
1 | WITH RECURSIVE |
exp:(很好的数论,让我的大脑短路)# 唉,乘法逆元。
1 | import sqlite3 |
TSGDBinary
题目分类
< ? >
题目信息
Author: iwashiira
Everyday Tools
三个文件,start.sh:
1 | sudo gdb --nx -x ./tsgdbinary.py ./tsgdbinary |
执行 tsgdbinary 二进制文件,同时将 tsgdbinary.py 作为 GDB 脚本加载
。。哭了
不想看了。先做点作业吧。
serverless
<\yaml><重定向>
题目分类
题目信息
Author: mikit
Experience the power of serverless computing.
The server is provided for illustration purposes only and there is no need to connect to the server to solve this task.
题目分析
不太懂是什么,可以看到后面都是格式相同的内容,把前面扔个chatGPT:写了一些注释:
1 | # docker-compose配置文件 |
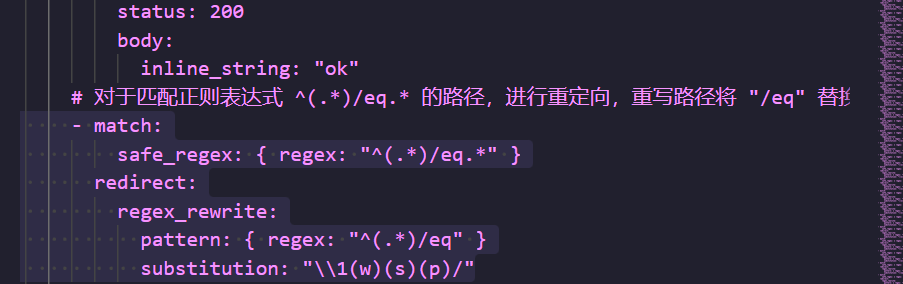
将六行匹配,写为一行的键值对,发现有以下规则:
- 标志开头的 TSGCTF{ 中的开头括号 %7B 被转换为(/ 和 “开头圆括号 + 斜线”。
- 标志末尾 } 的结尾括号 %7D 被转换为 a) 和结尾圆括号。
- 将 ) 转换为 ) 和结尾圆括号。 换句话说,去掉斜线。
- 将 _ 转换为)(/和 “闭合圆括号 + 开头圆括号 + 斜线”。
- 将 “斜线 + 1 或 2 个小写字母或数字或连字符”(如 /eq)转换为 “圆括号内的 3 个小写字母 + 斜线”(如 (w)(s)(p)/)。
- 将 “斜线 + 1 或 2 个小写字母、数字或连字符”(如 /6i)转换为 “3 个小写字母(用圆括号包围) + 3 个大写字母 + 斜线”(如 (s)(y)(n)RZK/)。
- 将 “斜线 + 1 或 2 个小写字母或数字或连字符”,如 /wz/ 转换为 “1 个小写字母 + 3 个大写字母 + 斜线”,如 cDPL/。
- 将 “大写字母 + 圆括号内的小写字母”(如 M(m))转换为空字符串。 这种组合适用于从 A 到 Z 的所有 26 个字母。
- (有些模式会将 %7D%7B 转换为 +。 但这种情况不会发生)。
对所有模式的分析表明,斜线的位置在模式中非常重要。
- 斜线由大括号和下划线产生。
- /eq 等模式在转换字符串(例如
/),并在斜线到达结尾圆括号时清除斜线。- 目标是重定向的结果是/。 为此,必须删除 TSGCTF 字符串。 考虑到可以删除的模式,TSGCTF(f)(t)(c)(g)(s)(t) 模式显然需要完成。
换句话说,对于字母 tsfctf,我们需要找到满足以下重定向的模式:。
- 第一个重定向目标是 tABC/ 格式中的 “1 个小写字母 + 3 个大写字母 + 斜线 ”模式
- 中间重定向目的地是(c)(b)(a)XYZ/格式的 “3 个小写字母括在圆括号中,抵消前面的 3 个大写字母 + 另外 3 个大写字母 + 斜线 ”模式的零次或多次重复。
- 最后一个重定向是(z)(y)(x)/,即 “3 个小写字母括在圆括号中,取消前面的 3 个大写字母 + 一条斜线”。
/をかお えすあ <–读出来就知道是哪个表情包了)
。为什么我这么菜啊我靠啊
。。
贴一个csome师傅的exp.py:
1 | #!/usr/bin/env python3 |

