关于汽车固件及逆向的一点学习
参考文章:
[T-BOX:车联网关键组件的演进与功能剖析-CSDN博客](https://blog.csdn.net/wteruiycbqqvwt/article/details/120526194#:~:text=1、TBOX作为量产件产生的最初原因是法规等要求的数据传输,但在法规未强制时,TBOX已经在车厂具备形态。 车,联网,是万物互联时代的大势所趋;,2、同时,TBOX是在基于传统车辆的功能和架构衍生出的新模块,因此, TBOX的功能定义、硬件形态等都具有架构的时代特征,与网络相关的功能,基本都是体现在TBOX上,比如远控、OTA、远程诊断等。 接下来从宏观到微观对T-BOX分析。)
车联网安全基础知识之TBOX主要功能 - IOTsec-Zone
这里是对资料内容的个人整理和一些思考
为什么要学习车联网呢,或许命运,或许选择
第一部分:
1. Introduction
Many cutting-edge technologies presented on this system, such as virtualization, TEE, augmented reality, etc
Earlier this year, Qihoo 360 published their research on Mercedes-Benz [7], which mainly focused on Mercedes-Benz ‘s T-Box, instead of the central infotainment ECU: head unit. The test bench showed in their presentation was built with an NTG5 head unit, which is a bit old.
In MBUX, the tested head unit version is NTG6 (being used in A-, E-Class, GLE, GLS and EQC). Our research was based on this brand new system MBUX, NTG6 head unit, and vehicle W177.
In our research, we analyzed many attack surfaces and successfully exploited some of them on head unit and T-Box. By combining some of them, we can compromise the head unit for two attack scenarios, the removed head units and the real-world vehicles. We showed what we could do after we compromised the head unit. Figure 1.1 demonstrates the compromisation of an actual car.
We didn’t find a way to compromise the T-Box. However, we demonstrated how to send arbitrary CAN messages from T-Box and bypass the code signing mechanism to fash a custom SH2A MCU firmware by utilizing the vulnerability we found in SH2A firmware on a debug version T-Box.
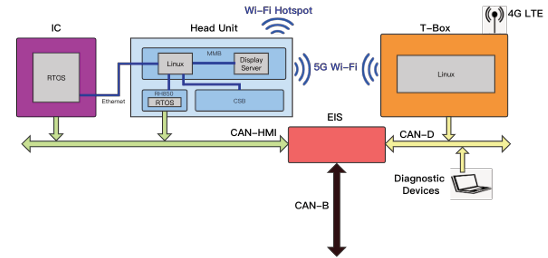
2. Architecture overview 结构概述
introduces the whole architecture overview about hardware, software, and CAN networks
Hardware
Head Unit 主机
Head unit’s version is NTG6. It plays a vital role in the MBUX infotainment system. It provides multimedia, navigation, voice control, and other functions.
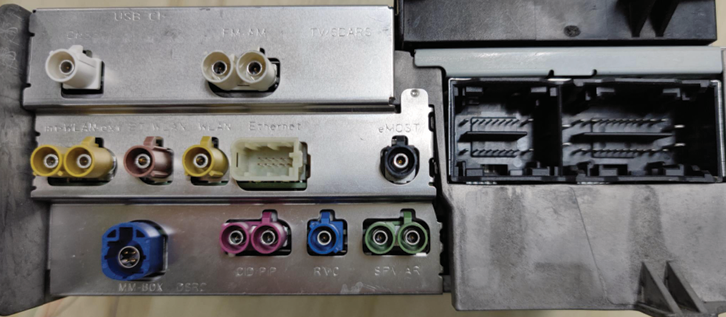
NTG6 head unit composes three main PCB boards inside. Vendor named them Multimedia Board(MMB), Base Board(BB) and Country Specific Board(CSB).
Multimedia Board(MMB)
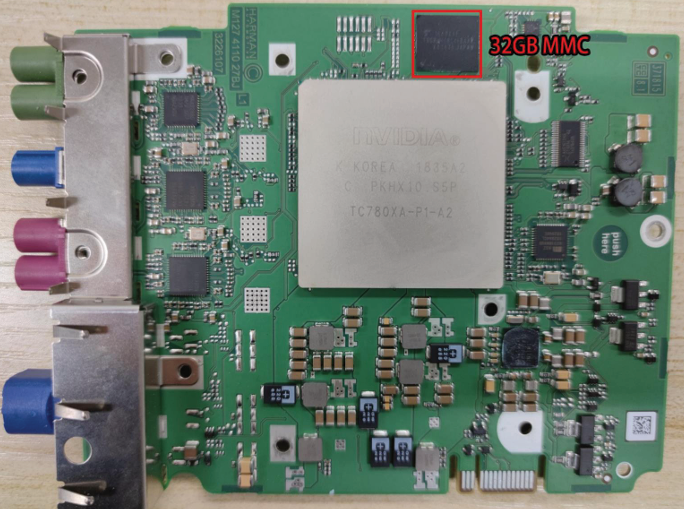
On Multimedia Board, there is a big Nvidia Parker SoC. Near the SoC, there is a 32GB MMC. This MMC stores the main file system of the head unit system.

After removing this SoC’s cooling shield, we can see 4 DRAM, a NAND flash chip, and its main processor. The NAND flash contains bootloader, hypervisor, and TEE related code and data
Base Board
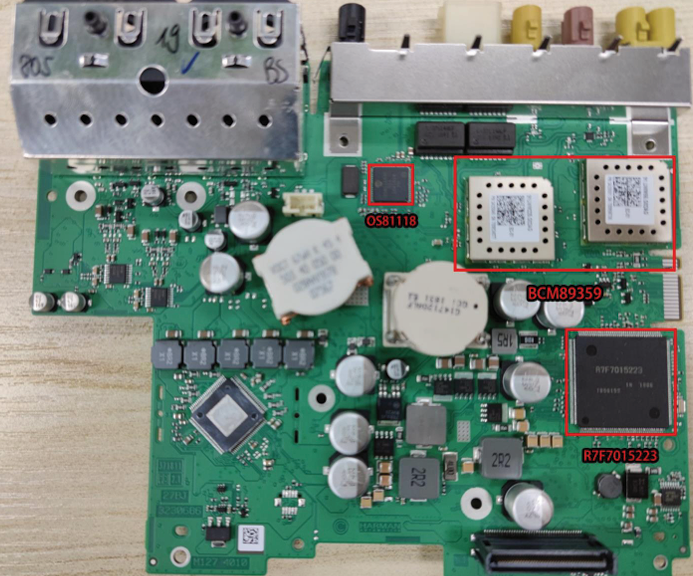
On the top side of the Base Board, there is an RH850 chip R7F7015223 from Renesas. It is mainly responsible for CAN transmission. One MOST interface controller OS81118, which provides the MOST network to the head unit operating system. Two 5G Wi-Fi chips BCM89359. One is for connections to passengers’ devices. The other one is for connections to T-Box
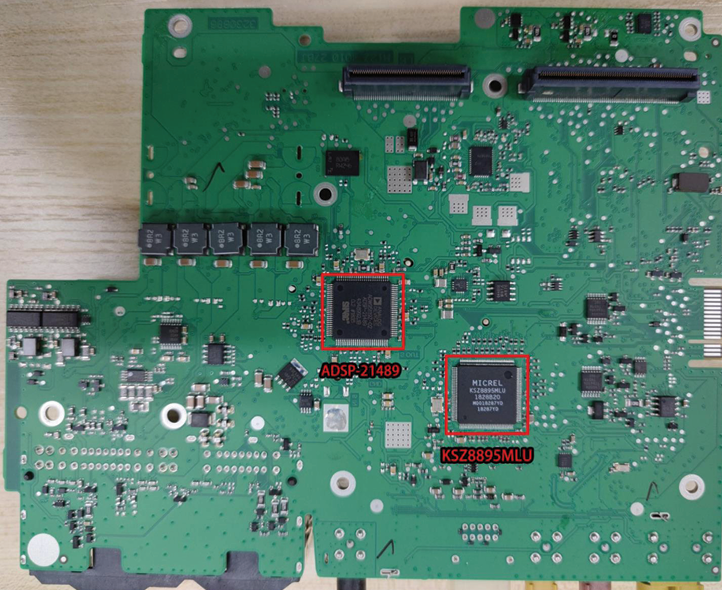
On the bottom side of the Base Board, there is a switch chip: KSZ8895MLU. This switch chip is the center of head unit Ethernet. Most of the system in head unit that requires Ethernet connects to this chip
There is a DSP chip from Analog Devices: ADSP-21489. According to our analysis, it is responsible for audio processing. The architecture is SHARC.
Country Specific Board
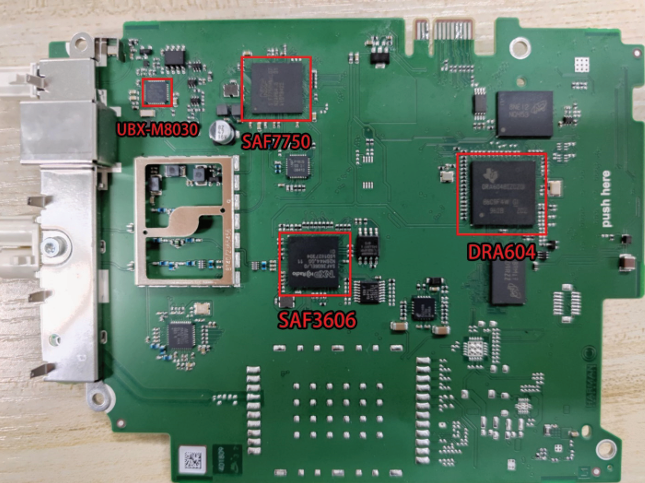
//?真假的?根据国家各异?
The Country Specific Board in head unit varies by country. The board in our head unit runs a Jacinto 5 Linux system. There is a radio solution from NXP, named Saturn. And there is a GNSS chip from u-blox.
T-Box
T-Box, it’s also called TCU or HERMES module. It connects the vehicle to LTE network, provides head unit internet connection, and receives vehicle control commands from the cloud server.

Electronic Ignition Switch 电子点火开关
The Electronic Ignition Switch(EIS) is the gateway ECU in the vehicle. It mainly contains two functions, the keyless function and the gateway function. According to our experiment, this ECU also acts as a firewall that filters CAN messages

Instrument Cluster 仪表盘
Figure 2.11 shows the instrument cluster ECU. There is an RH850 chip inside, which runs an RTOS. It connects to head unit with Ethernet and a video wire

Software
Head Unit
On the NTG6 head unit, the Multimedia Board consists of the Tegra T18X SoC. Therefore, the hardware can support the Nvidia Tegra hypervisor very well. The hypervisor virtualizes two Linux systems. One is the primary Linux system, and another is the display server. Besides, the Multimedia Board also supports Trusty TEE , which is used for encrypting some sensitive data of the system.
T-Box
//?啊?huawei designed???
On T-Box, the system runs on SoC ME919bs designed by Huawei. It is a Linux system, but similar to an Android in some ways. For example, the dynamic linker and the format of the boot image. Programs are developed by Harman and Huawei
CAN Network Overview CAN 网络概述
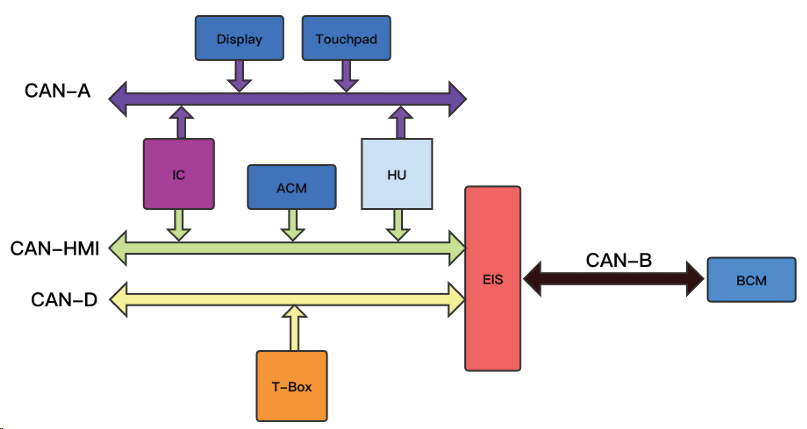
There are many CAN buses on Mercedes-Benz A200L cars. Figure 2.12 shows the overview of the CAN network.
3. Research Environment Setup 研究环境设置
describes our test bench setup, how we built a low-cost testing environment, how we collected ECUs and wired them up, and how we powered up our test bench.
Testing on a real car is convenient, but for a security test, testing on a test bench can reduce the risk of vehicle damage and provide more flexibility. We bought many infotainment ECUs for building our test bench, including four head units, server T-Boxes, and other ECUs.

In this chapter, we show our steps to assemble ECUs we bought into a working test bench.
Connecting ECUs
According to Mercedes-Benz software’s whole view of the wiring diagram, we wired the ECUs we bought. Figure 3.2 shows our test bench’s connection diagram.
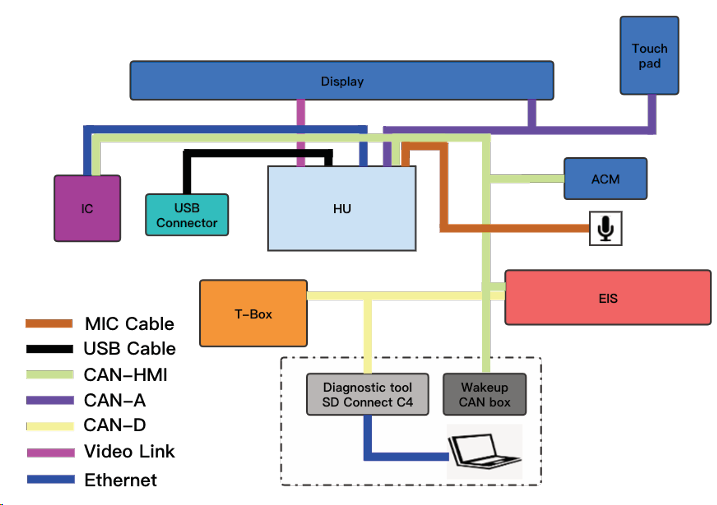
Wake Up Test Bench 唤醒测试台
The test bench won’t simply be powered on after connected to the power supply. In an actual car, when you ignite the engine, wake-up CAN signals come from CAN bus to power the head unit up.
We need to capture and replay these signals. We don’t have a real car to capture the signals at that time. However, we found that there are tiny boxes in the vehicle market that emit wake-up signals. We bought one of these boxes and successfully powered on our test bench.

Out of curiosity, we captured signals that came from this box. It emits three CAN signals periodically.
| ID | DATA |
|---|---|
| 0x25E | 64 64 64 00 03 00 00 00 |
| 0x2F7 | C2 50 10 57 12 5D 5F 53 |
| 0x020 | 39 C9 41 1C C0 00 00 C0 |
Connect this wake-up CAN box to CAN-HMI, head unit boots, and the screen lights up.
Anti-Theft 防盗
After the head unit booted up, it enters Anti-Theft mode. A notification UI layer covers the touch screen in this mode, preventing the user from operating on the screen. We will show our method of Anti-Theft unlocking in the following chapters

4. Attack Surfaces Analysis 攻击面分析
illustrates the potential attack surfaces on head unit and T-Box.
After the testing environment has been set up, we analyzed the attack surfaces of MBUX. In this chapter. We will list the common attack surfaces that exist on head unit and T-Box. We will also assess the difficulty and the possibility of compromising these attack surfaces. Figure 4.1 shows the attack surfaces we found on Mercedes-Benz A200L. We only tried some of the attack surfaces
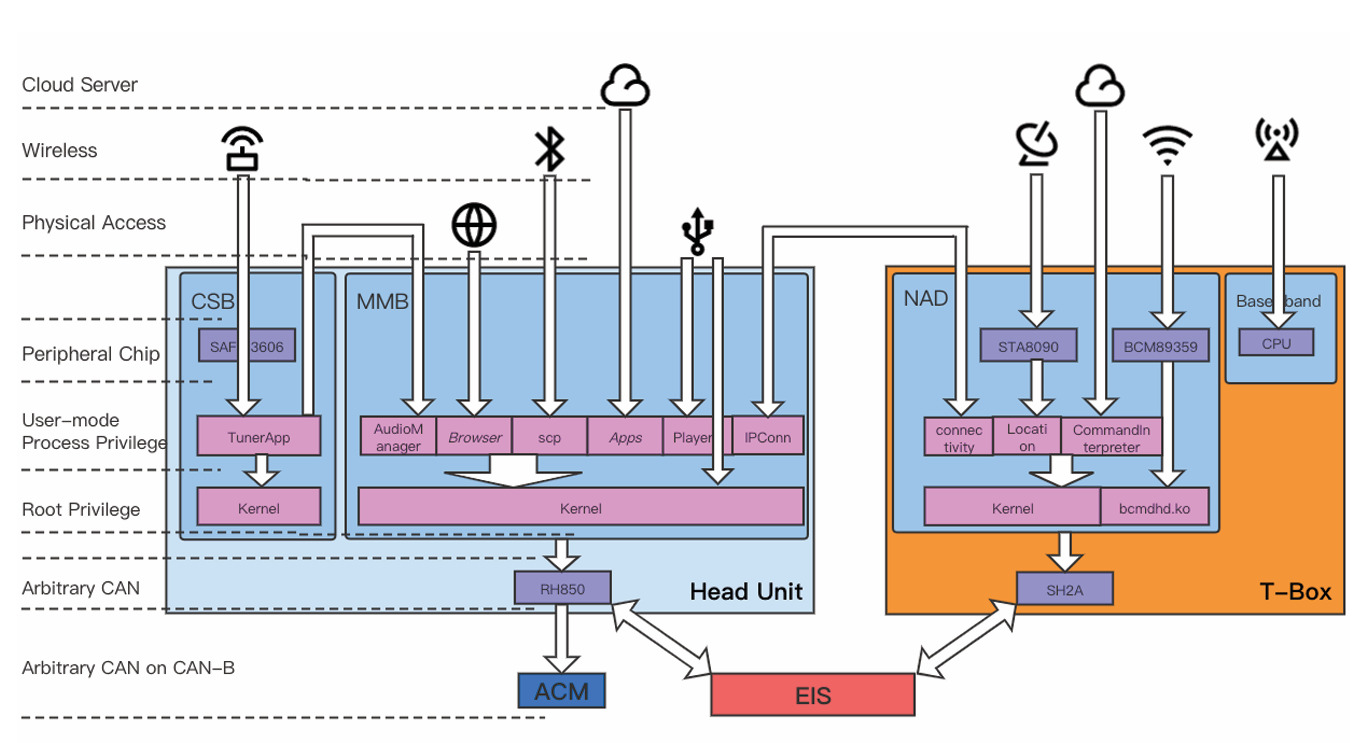
Head Unit 主机
Attack Through Browser 通过浏览器进行攻击
MBUX provides a browser application for the driver and passengers on the touch screen. From a security point of view, it opens a dangerous attack interface since the browser’s JavaScript engine is more likely to be vulnerable.
Wi-Fi
Attack Wi-Fi chip
In NTG6 head unit, there are two BCM89359 Wi-Fi modules on broad BB. The BCM89359 chip a 5G Wi-Fi/Bluetooth Smart 2X2 MIMO Combo Chip. One is used to set up an AP for passengers. The other is used to set up an AP for T-Box.
In the year 2020, we published a research about the Wi-Fi Stack on Tesla. The research demonstrates two attack surfaces belong to an attack chain, from wireless packet to Wi-Fi chip and from Wi-Fi chip to host system. For NTG6 head unit, the two attack vectors are different.
For the first attack vector that from wireless packet to Wi-Fi chip, a vulnerability should be found in the Broadcom BCM89359 firmware. Project zero published their researches on Broadcom Wi-Fi firmware and showed how to exploit the Broadcom firmware vulnerability. We didn’t reproduce such a kind of attack on NTG6 head unit
Attack from Wi-Fi chip to Host system
On NTG6 head unit, the Wi-Fi chip connects to the host system via the PCI-E interface. According to project zero’s research, it is possible to perform a DMA attack to write the host’s physical memory directly if the host does not enable IOMMU or VT-d. On NTG6 head unit, the host system is launched by the Nvidia hypervisor. What’s important is that the IOMMU is enabled. Eventually we didn’t achieve a successful exploit. In the worst case, the hypervisor will panic.
Kernel
The version of the Linux kernel in the system is 3.18.71, which is outdated. In our research, We utilized a kernel vulnerability to achieve privilege escalation.
Ports on MMB MMB 上的端口
The CSB system and MMB system are both Linux systems. They can communicate through Ethernet. Their IP addresses belong to the subnet 192.168.210.109/30. Many TCP or UDP ports on the MMB system can be accessed by CSB. For example, the radio information is transferred through a TCP socket. Therefore, there are many attack vectors from CSB
Bluetooth
Head unit provides Bluetooth functions to passengers. If there are vulnerabilities in Bluetooth stack, it’s possible to achieve code execution in head unit. We demonstrated this kind of attack in our Lexus research[2]. We didn’t focus on Bluetooth this time on Mercedes-Benz.
USB
As far as we know, head unit supports USB sticks. There is code to save user configurations and system logs to USB sticks. Also, there is code to read map data and Point of Interest(POI) data from a USB stick. Improper handling of these data can lead to security risks.
Head unit supports Carplay, Android Auto, MirrorLink, and CarLife. These functions can be accessed via USB. If there are vulnerabilities in any of these functions, it will be possible to attack head unit through USB.
App
Nowadays, vendors like to put third-party apps in their head unit. According to our previous experience, third-party apps are prone to Man-In-the-Middle attacks.
Mercedes-Benz also supports third-party Apps, which communicate with remote servers. The functions of these Apps are very limited. We didn’t test this attack surface in our research because the Apps in our test bench are not working
**T-Box **
Attack Through Wi-Fi Chip
On T-Box, the vendor of the wireless chip is Broadcom, and the model is bcm4359. Inspired by Project Zero’s research, we also investigated if the T-Box is vulnerable to the same DMA issue. The chip can overwrite arbitrary physical memory unlimited since this bcm4359 connects to the host system through the PCI-E bus
Attack Through GNSS
On T-Box, there is a chip STA8090 which is a single die standalone positioning receiver IC (单晶片独立定位接收器 IC)working on multiple constellations. This chip connects to the host system via serial. The process Location receives NMEA messages from the STA8090 through this serial.
The firmware can be found from the file system. It is an RTOS system based on OS20. Therefore, there are two attack vectors. The first one is from wireless to STA8090 chip. The second one is to attack the host system from the STA8090 chip through serial.
CAN
On Mercedes-Benz A200L Cars, T-Box connects to CAN bus CAN-D. The SH2A chip is responsible for transmitting and receiving CAN messages between the Linux system and CAN bus. Therefore, a difficult attack surface is that attacking the SH2A chip from the CAN-D bus.
Additionally, some processes will process the message wrapped by CANTP protocol or other protocol. It gives the attacker a chance to attack the user mode process from the CAN bus
Baseband.
The T-Box utilizes Huawei’s LTE solution me919bs. It means the baseband is balong and the firmware for cellular baseband locates on T-Box’s file system.
In 2017, we compromised Huawei’s balong baseband in pwn2own. We found in T-Box firmware version E311, the bug we used in pwn2own exists.
We set up the environment we used in pwn2own. But we found that the T-Box wouldn’t connect to our station. The T-Box uses UMTS but not CDMA2000. The bug we used in pwn2own lays in CDMA2000 protocol stack. Although the code contains the bug, it cannot be triggered.
We tried to find other bugs by analyzing the balong firmware. Besides the leaked source code online, we found that the firmware contains a symbol table. In this symbol table, there are function names, function addresses, and function sizes. The symbols helped us a lot in understanding the firmware.
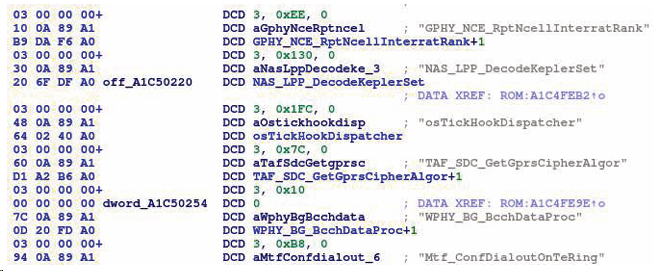
Later we upgrade T-Box firmware to E511. The new baseband firmware introduced more security mitigations and fixed the bug we used in pwn2own, which made it very difficult for us to attack from base band.
GSM hijack GSM 劫持
T-Box receives vehicle control commands from a remote server via the cellular network. Vehicle control commands can be received by T-Box via HTTPS, MQTT, or GSM text messages. T-Box verifies server identifications in HTTPS and MQTT. So hijacking vehicle control commands in these two protocols is not possible.
T-Box connects to the cellular station via LTE. We can downgrade it to GSM and make T-Box connects to our base station. We set up a base station using USRP and OpenBTS. After T-Box connected to our station, we can send GSM text messages to T-Box.
We analyzed the vehicle control message format and found that the message is signed by Mercedes-Benz’s private secret key. And it is authenticated inside T-Box. Without the private secret key, we are unable to construct a valid vehicle control message. We analyzed the cryptography algorithm and did not found any weakness.
We then reversed the code and tried to find memory corruption bugs in the SMS handling code. However, we did not find exploitable bugs.
5. Compromise Head Unit
presents the details of four attack surfaces of head unit in the direction from the outside to the internal system This chapter presents the details of four attack surfaces of head unit in the direction from the outside to the internal system, including how we connected to the head unit’s intranet by soldering wires on the PCB, how we achieve remote code execution in head unit by exploiting the HiQnet protocol and the browser. Finally, we will details how to achieve local privilege escalation in head unit
Access to the Intranet of Head Unit 访问总部内联网 .
Connect to Head Unit as T-Box 以 T 形盒式连接至主机
Connect to MMB as CSB 作为 CSB 连接至 MMB
Remote Code Execution on Head Unit 在主机上执行远程代码
Implementation of HiQnet Protocol 实施 HiQnet 协议
Vulnerabilities in HiQnet Protocol HiQnet 协议中的漏洞
Exploit HiQnet Protocol Vulnerability 利用 HiQnet 协议漏洞
Exploit the Browser 利用浏览器
QtWebEngine
Exploit the QtWebEngine
Local Privilege Escalation 本地权限升级
Kernel LPE with A perf Bug 内核 LPE 存在灌注错误
CVE-2017-6786,6001
Bypass Cgroups Restriction 绕过 C 组限制
6. Post Attack in Head Unit Head设备的攻击
will discuss the potential impact after the head unit is compromised. For example, we can tamper with the images displayed on the screen and perform some vehicle actions after we compromised the head unit.
Anti-Theft Unlock 防盗解锁
Unlocking Vehicle Functions 解锁车辆功能
Engineering Mode 工程模式
Persistent Backdoor 持久后门
Display Screen Tampering 篡改显示屏
RH850 Denial of Service RH850 拒绝服务
Perform Vehicle Control Actions 执行车辆控制操作
7. Compromise T-Box
This chapter shows two attack attempts for two attack surfaces, the Wi-Fi and CAN bus of T-Box in the direction from the outside to the internal system.
Compromise Host from Wi-Fi chip 从 Wi-Fi 芯片破坏主机
Trigger Memory Corruption From SH2A Chip 从 SH2A 芯片触发内存破坏
Message Format between SH2A MCU and Host SH2A MCU 和主机之间的信息格式
The message packet between SH2A MCU and Host consists of header and body. The size of the header is 8 bytes, and its format is shown in Figure
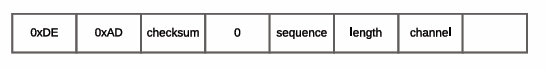
The first two bytes are fixed. The 6th byte is the length of the payload. The 7th byte represents the channel number of this packet. The format of payload varies by the number of channels.
Out-of-bound Vulnerability in RemoteDiagnosis .RemoteDiagnosis 中的越界漏洞
The process RemoteDiagnosisApp registered channel 10 RemoteDiagnosis with blockIpcServer. There is a vulnerability when the process RemoteDiagnosisApp parses the payload of channel 10 sent by SH2A MCU and transferred by blockIpcServer. The payload of channel 10 is shown in Figure 7.4
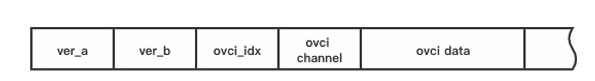
An array OOB read exists in function get_ovci_chn, which is shown in Figure 7.5.
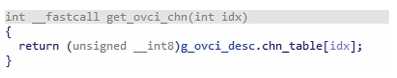
The size of the array chn_table is 88. Therefore, if the argument idx is above 88, an OOB read happens. The table array chn_table contains the channel index related to the ovci index. This means the result returned from function get_ovci_chn() may be above 1, according to the data outside the array. Then the ovci_data is stored in the ovci_data_area array, resulting in an OOB write. The code to trigger OOB write shows in Figure 7.6.

According to the memory layout, some structures and pointers can be overwritten outside the array chn_table. On T-Box version E511.6, pointers are more random than version E334.2 since ASLR is enabled on version E511.6. We didn’t try to exploit this vulnerability on version E511.6
8. Post Attack in T-Box 在 T-Box 中发布攻击
describes two attack processes that target the SH2A MCU on T-Box. By utilizing the vulnerabilities in SH2A firmware, we can send arbitrary CAN messages to CAN-D CAN bus and ash a custom firmware on SH2A MCU.
Sending Arbitrary CAN message from T-Box从 T-Box 发送任意 CAN 报文
CAN Bus Message Transmit Logic CAN 总线报文发送逻辑
Vulnerability in SH2A Firmware SH2A 固件中的漏洞
Transmit Arbitrary CAN Message to CAN Bus 向 CAN 总线发送任意 CAN 报文
Flashing Custom Firmware on SH2A MCU 在 SH2A MCU 上闪烁自定义固件
Firmware Downgrade Vulnerability 固件降级漏洞
Bypass Code Signing Check During Upgrading 在升级过程中绕过代码签名检查
9. Exploratory Research 探索性研究
demonstrates our research on the hardware module Country Specific Board and Airbag Controller Module. We will introduce the research on digital radio and the search process of the Airbag Controller Module.
Digital Radio Research 数字无线电研究
FM
Digital Audio Broadcasting
Airbag Research
Compromise Scheme
10. Verified attack chains 经过验证的攻击链
we analyze the potential attack chains by combining the potential attack surfaces. We successfully verified each of the head unit’s attack chains, the removed infotainment compromise scheme, and the actual vehicle compromise scheme. Also, we mention the unrealized attack chains in our research
For a Removed head unit
For a Real Vehicle
Unrealized Attack Chains 未实现的攻击链
From Wi-Fi to Vehicle Control - 1.
From Cellular Network Hijack to Vehicle Control - 2
From Radio to Airbag Control Module - 3 .
From Head Unit to T-Box - 4
Target Version 目标版本
Vulnerabilities List 漏洞列表
Conclusion
第二部分:T-Box架构
硬件构架
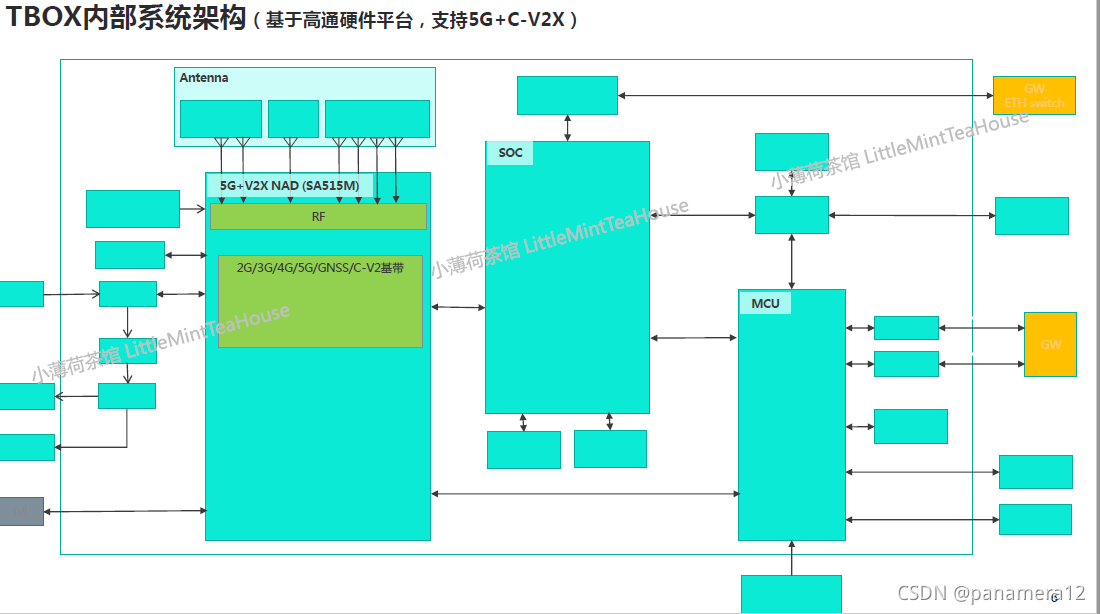
软件
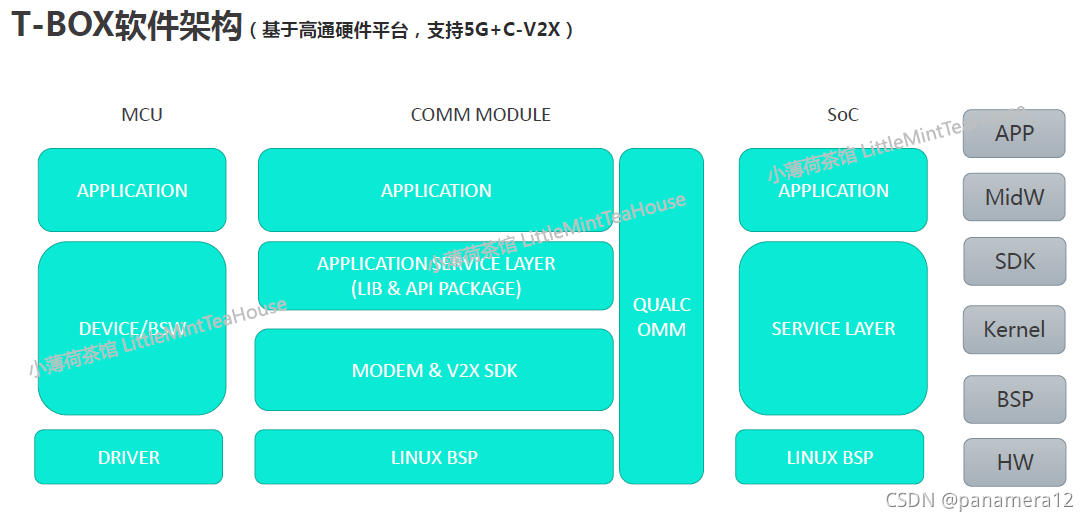
组件
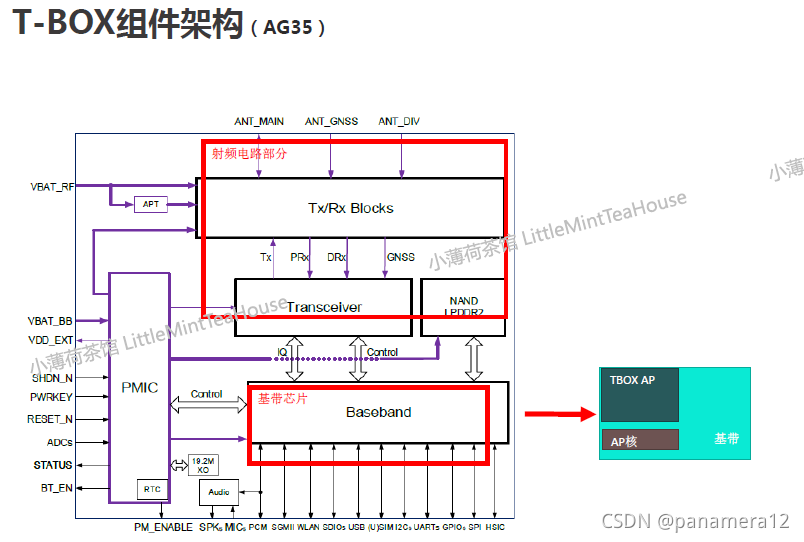
网络
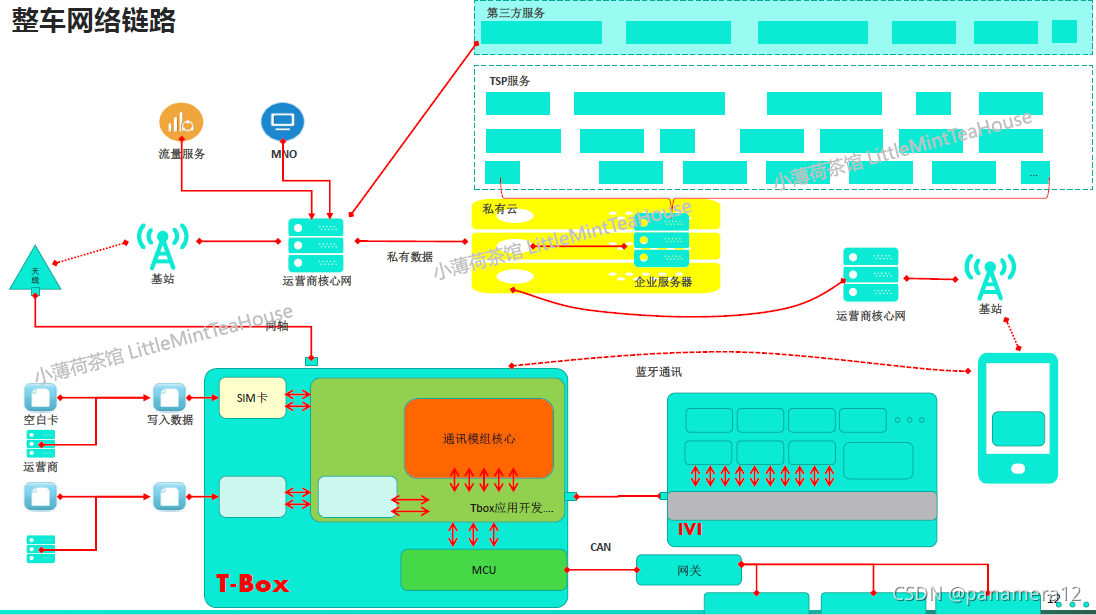
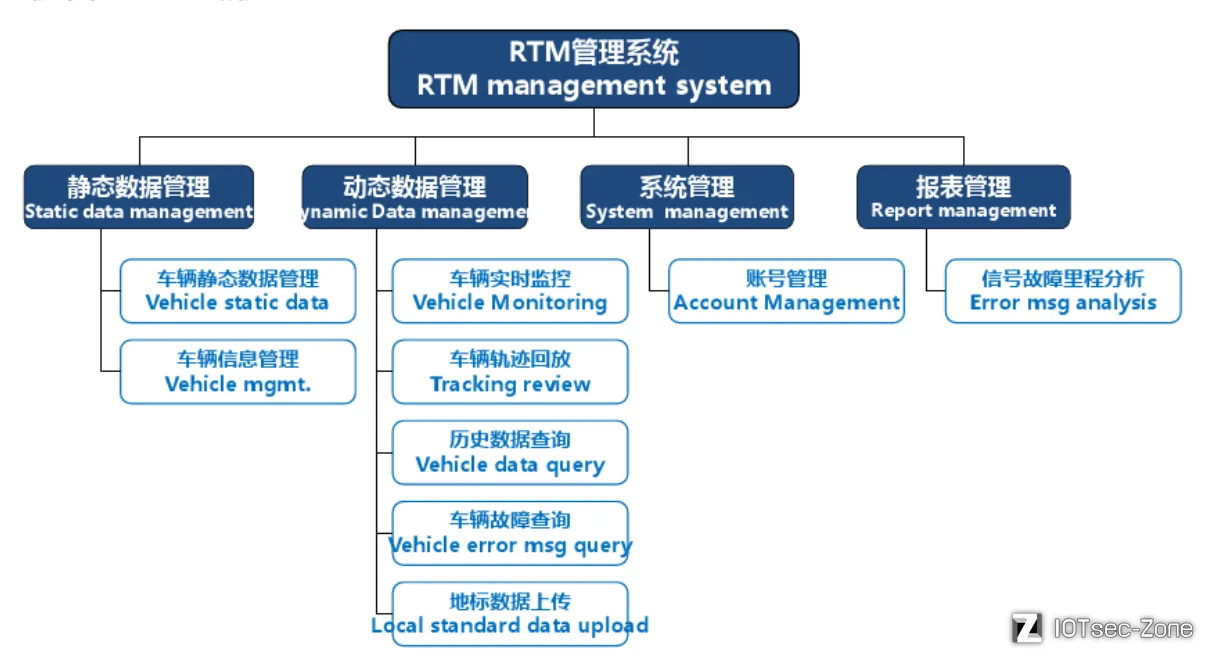
第三部分: Tbox主要功能
车联网安全基础知识之TBOX主要功能 - IOTsec-Zone
TBOX 提供的功能有网络接入、OTA、远程控制、位置查询/车辆追踪、电池管理、位置提醒、eCall、远程诊断、平台监控/国家监管等。
实时监控: